Why is Social Engineering Dangerous?
- Difficult to Detect: Exploits human behavior rather than technical vulnerabilities.
- Widespread Impact: Can affect individuals, businesses, and governments.
- Low-Cost Attack: Requires minimal resources compared to traditional hacking.
- Bypasses Security Measures: Even strong firewalls and antivirus software can’t stop social manipulation.
Common Social Engineering Techniques
1. Phishing
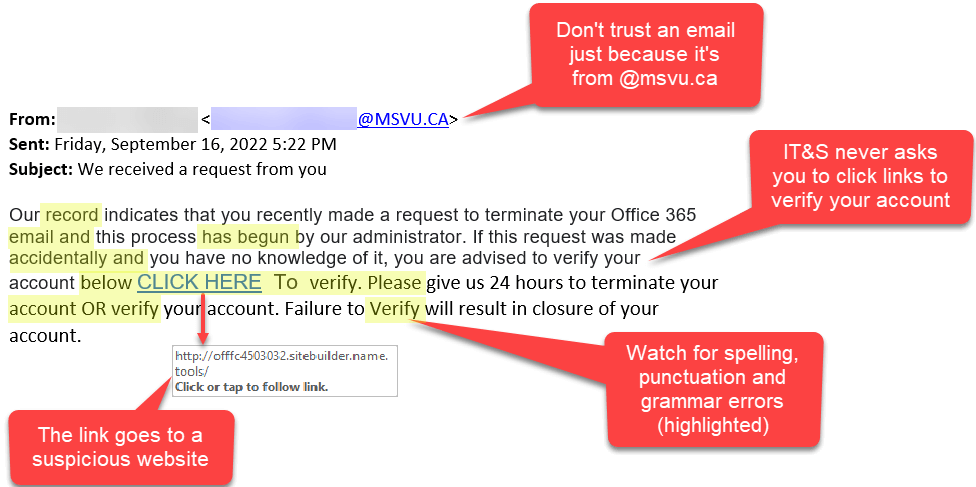
Phishing involves sending fraudulent emails or messages that appear legitimate, tricking users into providing sensitive information. Example:- An email posing as a bank, asking you to update your password via a fake link.
How to Protect Yourself:
- Verify sender addresses before clicking on links.
- Use multi-factor authentication (MFA).
- Never provide personal information via email.
2. Vishing (Voice Phishing)
Attackers use phone calls to impersonate trusted entities, such as tech support or financial institutions, to extract sensitive information. Example:- A scammer pretending to be from Microsoft calls, claiming your computer has a virus and asking for remote access.
How to Protect Yourself:
- Be skeptical of unsolicited calls requesting information.
- Hang up and call the official number of the organization.
- Never share passwords or OTPs over the phone.
3. Pretexting
Pretexting involves an attacker creating a fabricated scenario to trick victims into revealing confidential information. Example:- A scammer posing as an IT support staff requesting login credentials to fix an issue.
How to Protect Yourself:
- Verify the identity of the requester.
- Do not share personal information unless absolutely necessary.
- Follow company security policies.
4. Baiting
Baiting involves enticing victims with something appealing, such as free software or USB drives, which contain malware. Example:- A USB drive labeled “Employee Salaries” left in a company parking lot, tempting employees to plug it into their work computer.
How to Protect Yourself:
- Avoid plugging in unknown USB devices.
- Download software only from trusted sources.
- Use endpoint security solutions.
5. Tailgating (Piggybacking)
Tailgating occurs when an unauthorized person gains physical access to a restricted area by following an authorized individual. Example:- An attacker follows an employee into a secure building without using an access badge.
How to Protect Yourself:
- Always ensure doors close behind you.
- Challenge unfamiliar individuals in secure areas.
- Use badge access control policies.
The Social Engineering Attack Lifecycle
How to Defend Against Social Engineering Attacks
- Security Awareness Training: Educate employees and individuals about common scams.
- Multi-Factor Authentication (MFA): Adds an extra layer of security.
- Zero-Trust Policy: Verify everything before granting access.
- Use Secure Communication Channels: Avoid sharing sensitive information over unsecured networks.
- Report Suspicious Activities: Encourage prompt reporting of potential attacks.

